johndave_theone
Addict
salamat sa share sirr
mga sir paturo po plz...anjan napo ang mga tutorial wag nalang ikalat pa
wait nalang sa update po sir
abang ka ng update baka sa isang linggo pa update nito pero ma vbs cripf naman na jan para makakuha kayo ng cert. ang prvte kêy sa mac na ma scan nyo
Download ko sir for future porpuses, samamat.UPDATE MAC SNIPING
As of June 26, 2014 the PLDT/Smart Telco 4G wireless Internet Service Provider made its first clearing operation on its network and wireless system to eliminate the country's number one rampant in cloning the 4G wireless broadband CPEs. According to this forum the usual MAC address base authentication of the SMART myBRO 4G wireless modem is no long effective as of the said date, this is because the AAA is already been implemented such as the Device Certificate + Private kêy + MAC address, if this three is not much on your Green Packet device such as DV235T and OX230 then you will no longer be welcome to the network. In short you will be denied to access to the Smart 4G Base Station, there's no way for you to use even the proxy server to bypass their portal.
Here's simple step on how to retrieve your myBRO 4G wireless broadband modem device certificate, private kêy and the mac address either via telnet or ssh make sure to enable port 23 or 22 to be able to get this terminal open.
Once you are login to the command line interface (cli) e.g. telnet or ssh, just type this following command respectively.
cd /etc
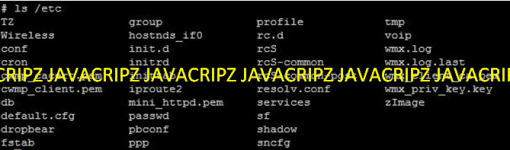
The ls /etc command is to view the list directory of the /etc now you will be able to see the filename wmx_client_ca.pem this is the device certificate and the wmx_priv_key.kêy filename is the private kêy.
cat wmx_client_ca.pem
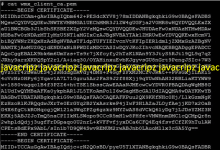
cat wmx_priv_key.kêy
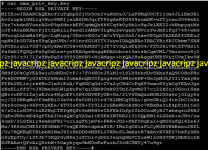
After you have viewed the device certificate and the private kêy in plain text, you can copy paste this to notepad and save it as wmx_client_ca.pem, wmx_priv_key.kêy filename respectively. Now you already successfully retrieved your myBRO device certificate likewise the private kêy.
Additionally, the next command is if you wanted to retrieve your myBRO 4G wireless broadband WAN MAC address just type this command and you will prompted your device WAN MAC.
sncfg get WAN_MAC
have included this extra screenshot because of some myBRO 4G Wireless broadband CPEs their device certificate and private kêy are hidden, just like on this screen. The Green Packet equipment which Chipset is MediaTek is embedded with Linux OS and therefore it is equip with tiny all in one Busybox you can use the tool to unhide the device certificate and the private kêy.
PARA NAMAN DI KA MAHIRAPAN dôwnlôad MO NALANG YUNG TUTORIAL NASA ATTACH MENT PO..
balita dito? may nakapag unhide naba ng mga certificates sa pem and kêy? may tool or script ba para makita ung wmc_client.pem sa mga telnet ...
sir enge nga po tut, para mareconnect ko ung dv ko sa new updates ng smart. newbie lang po kasi ako..
sana di yan magamit sa panluluko ng kapwa mga master...di katulad ng nasa unang comment..comsatkid man luluko yan....wag kau manilawa sa taong yan...