Khim Briones
Forum Expert
- Joined
- Aug 22, 2013
- Posts
- 3,118
- Reaction
- 16,686
- Points
- 2,419
UPDATE MAC SNIPING
As of June 26, 2014 the PLDT/Smart Telco 4G wireless Internet Service Provider made its first clearing operation on its network and wireless system to eliminate the country's number one rampant in cloning the 4G wireless broadband CPEs. According to this forum the usual MAC address base authentication of the SMART myBRO 4G wireless modem is no long effective as of the said date, this is because the AAA is already been implemented such as the Device Certificate + Private Key + MAC address, if this three is not much on your Green Packet device such as DV235T and OX230 then you will no longer be welcome to the network. In short you will be denied to access to the Smart 4G Base Station, there's no way for you to use even the proxy server to bypass their portal.
Here's simple step on how to retrieve your myBRO 4G wireless broadband modem device certificate, private key and the mac address either via telnet or ssh make sure to enable port 23 or 22 to be able to get this terminal open.
Once you are login to the command line interface (cli) e.g. telnet or ssh, just type this following command respectively.
cd /etc
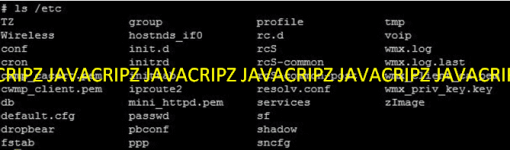
The ls /etc command is to view the list directory of the /etc now you will be able to see the filename wmx_client_ca.pem this is the device certificate and the wmx_priv_key.key filename is the private key.
cat wmx_client_ca.pem
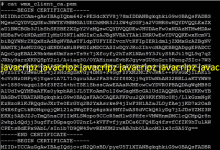
cat wmx_priv_key.key
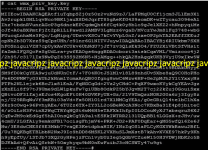
After you have viewed the device certificate and the private key in plain text, you can copy paste this to notepad and save it as wmx_client_ca.pem, wmx_priv_key.key filename respectively. Now you already successfully retrieved your myBRO device certificate likewise the private key.
Additionally, the next command is if you wanted to retrieve your myBRO 4G wireless broadband WAN MAC address just type this command and you will prompted your device WAN MAC.
sncfg get WAN_MAC
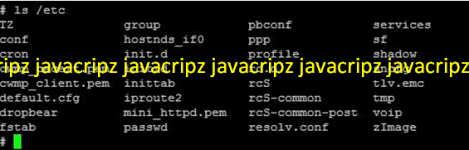
have included this extra screenshot because of some myBRO 4G Wireless broadband CPEs their device certificate and private key are hidden, just like on this screen. The Green Packet equipment which Chipset is MediaTek is embedded with Linux OS and therefore it is equip with tiny all in one Busybox you can use the tool to unhide the device certificate and the private key.
PARA NAMAN DI KA MAHIRAPAN DOWNLOAD MO NALANG YUNG TUTORIAL NASA ATTACH MENT PO..
As of June 26, 2014 the PLDT/Smart Telco 4G wireless Internet Service Provider made its first clearing operation on its network and wireless system to eliminate the country's number one rampant in cloning the 4G wireless broadband CPEs. According to this forum the usual MAC address base authentication of the SMART myBRO 4G wireless modem is no long effective as of the said date, this is because the AAA is already been implemented such as the Device Certificate + Private Key + MAC address, if this three is not much on your Green Packet device such as DV235T and OX230 then you will no longer be welcome to the network. In short you will be denied to access to the Smart 4G Base Station, there's no way for you to use even the proxy server to bypass their portal.
Here's simple step on how to retrieve your myBRO 4G wireless broadband modem device certificate, private key and the mac address either via telnet or ssh make sure to enable port 23 or 22 to be able to get this terminal open.
Once you are login to the command line interface (cli) e.g. telnet or ssh, just type this following command respectively.
cd /etc

The ls /etc command is to view the list directory of the /etc now you will be able to see the filename wmx_client_ca.pem this is the device certificate and the wmx_priv_key.key filename is the private key.
cat wmx_client_ca.pem

cat wmx_priv_key.key

After you have viewed the device certificate and the private key in plain text, you can copy paste this to notepad and save it as wmx_client_ca.pem, wmx_priv_key.key filename respectively. Now you already successfully retrieved your myBRO device certificate likewise the private key.
Additionally, the next command is if you wanted to retrieve your myBRO 4G wireless broadband WAN MAC address just type this command and you will prompted your device WAN MAC.
sncfg get WAN_MAC

have included this extra screenshot because of some myBRO 4G Wireless broadband CPEs their device certificate and private key are hidden, just like on this screen. The Green Packet equipment which Chipset is MediaTek is embedded with Linux OS and therefore it is equip with tiny all in one Busybox you can use the tool to unhide the device certificate and the private key.
PARA NAMAN DI KA MAHIRAPAN DOWNLOAD MO NALANG YUNG TUTORIAL NASA ATTACH MENT PO..
Attachments
-
You do not have permission to view the full content of this post. Log in or register now.
Last edited: