
With Hollywood’s glamorisation of häçking, it’s easy to think of häçker groups as some kind of romantic back-room revolutionaries. But who are they really, what do they stand for, and what attacks have they conducted in the past?
We see the stories every week of some intrepid häçker or häçker group wreaking havoc with their technical knowhow. Banks robbed of millionsthanks to some cryptic malware, or häçked documents leaked from a multi-national corp. This is without mentioning the millions of small-time websites and innocent (and more sinister) Twitter accounts being taken offline. The examples go on and on. But when you look into it, a good deal of the major attacks can often be attributed to a few prominent häçker groups.
Let’s take a look at a few of these groups, and what motivates them.
Anonymous: Decentralized Yet United
By far the most notorious and well-publicised häçker group is Anonymous. This is an underground, international network of nigh-anarchistic ‘häçktivists’ which sprung from 4Chan, the controversial image-based bulletin board. The collective has been known to the public since 2008 when it released a YøùTùbé video (above) setting the tone for what was to come. It was in this video that the group’s would-be tagline was uttered for the first time.
Knowledge is free. We are Anonymous. We are Legion. We do not forgive. We do not forget. Expect us.
In his first interview since becoming an FBI informant, former Anonymous member Hector Monsegur explains “Anonymous is an idea. An idea where we could all be anonymous…We could all work together as a crowd — united — we could rise and fight against oppression.”
Since then, the mysterious group has launched numerous attacks on the websites of government departments, politicians, multi-nationals, theChurch of Scientology, and hundreds of ISIS Twitter accounts (to name but a few). It’s important to note however, that due to Anonmyous being entirely decentralised, there’s no specific ‘leadership’ spearheading these campaigns. Most attacks will consist of entirely different individuals who could even be working toward their own individual ends.
One of the group’s most far-reaching campaigns was the attack launched against PayPal, VISA and Mastercard (Operation Avenge Assange) in response to the leash that was hung around the neck of Wikileaks.
In effect, Wikileaks was — and still is — dependent on donations to stay afloat. The US government mobilised plans to make these donations almost impossible, thereby strangling the website’s ability to stay in operation. Anonymous didn’t like this move, so countered it by making (very) effective use of the Low Orbit Ion Cannon (LOIC) tool. This tool allowed pretty much anyone to help out with the Denial-Of-Service (DDOS) attacks on these gargantuan websites, temporarily bringing them to their knees, and losing the companies millions of dollars in the process.
After the arguable ‘success’ of this attack, Anonymous started operating in a much more political sphere, attacking Mexican drug cartels (which failed), websites linked with child ****ography and Israeli government websites (in response to it’s attacks on Palestine).
The way in which Anonymous launches these attacks has become almost tradition for the group: the DDOS attack. This is where a website’s server is flooded with so much data (packets) that it can’t handle the pressure. Generally, the site goes offline until some techies come along to fix the problem, or until Anonymous cease the bombardment. In his fantastic NewYorker piece about Anonymous, David Kushner cites the former Anon Christopher Doyon’s military approach to the group’s DDOS attacks:
PLF: ATTENTION: Everyone who supports the PLF or considers us their friend—or who cares about defeating evil and protecting the innocent: Operation Peace Camp is LIVE and an action is underway. TARGET: You do not have permission to view the full content of this post. Log in or register now. Fire At Will. Repeat: FIRE!
The tactics of Anonymous do go beyond these ‘traditional’ DDOS attacks, though. Back in 2011, Anonymous’ attention turned to Tunisia (Operation Tunisia). Using the contacts and skills at their disposal, the group ensured the revolution happening on the streets received ample media coverage, häçked government websites, and distributed ‘care packages’ to protestors. These care packages have since been distributed at various rallies around the world, offering scripts that can be used to prevent government interception, among other things a revolutionary may need.
In terms of the overall aims of Anonymous, these were pretty clearly outlined in a statement publicising Operation Avenge Assange. Whether the group is going about realising these aims in the right or wrong way is open to debate but it’s certainly a step away from the ‘doing it for the LULZ‘ approach that many people associate with other acts of civil disobedience.
While we don’t have much of an affiliation with WikiLeaks, we fight for the same reasons. We want transparency and we counter censorship….This is why we intend to utilize our resources to raise awareness, attack those against and support those who are helping lead our world to freedom and democracy.
Syrian Electronic Army (SEA): Supporting Bashar al-Assad
Not all häçkers are fighting for more left-wing, liberal ideals, however. Back in 2012, Anonymous and the Syrian Electronic Army begun exchanging attacks and threats, which lead to Anonymous ‘declaring cyberwar‘ on the SEA (see the above video, and the SEA’s reply here)
Since 2011, the highly active SEA has been acting out of support for President Bashar al-Assad’s Syrian regime. Logically therefore, the SEA are often seen attacking Western media outlets that publish anti-Syrian messages. The university students (claimed to have connections with Lebanon-based Islamist militant group Hezbollah) behind these attacks have gained some respect from online security firms after häçking hundreds of websites. Prominent targets include the New York Times, CBC, and The Washington Post, causing many to be deeply concerned about the political motives behind the group.
By using malware, DDOS attacks, defacement, spamming and phishing, the patriotic team has been prolific in both attacks, and pranks. On the lighter side of the spectrum, when the group häçked the BBC Weather’s Twitter account, not much damage was done:
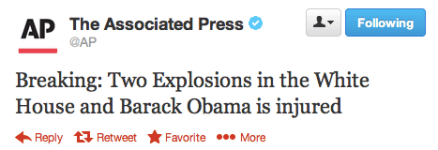
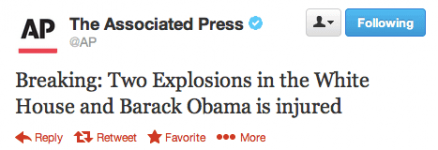
On the darker side, the group is well known for using spear-phishing attacks to gain login credentials to Gmail accounts, social media profiles, and more. On 23 April 2013 this approach lead to a Twitter hoax from the Associated Press news agency’s account. It was falsely stated that an explosion had happened in the White House, with President Obama being injured in the blast. A harmless prank at first thought, but in reality, this led to a $136bn drop on the S&P 500 index over a period of around 2 minutes.
To delve even deeper into the rabbit hole, the SEA has also been linked with posing as female supporters of Syrian rebels in order to s†éál war plans to use in the country’s ongoing conflict, leading to the death of a large number of rebels.
Chaos Computer Club (CCC): Revealing Security Flaws
It’s important to understand that not all häçker groups insist on using almost exclusively îllégâl measures to get their point across. A case in point is the Chaos Computer Club. As far as European häçker groups go, they don’t come any bigger than the CCC. which currently has well over 3000 members. Since it’s inception in Berlin during the early 1980s, the group has been pushing it’s personal brand of liberal ethics wherever it can.
This famously began when the CCC stole 134,000 Deutsch Marks from a bank in Hamburg by taking advantage of it’s online Bildschirmtext page, only to return the money the following day to highlight security flaws in the systems.
As mentioned, the majority of the group’s attacks, unlike other häçker groups, have primarily (but not always) been legal. In his interview withOWNI, Andy Müller-Maguhn, an early member of the CCC, explains that “we needed a lot of legal experts to advise us what we could or could not häçk, and to help us distinguish between legal activities and grey areas of legality”. This more benevolent approach to häçking has, according to Müller-Maguhn, lead to the CCC becoming “an accepted and recognized entity because it has worked to educate the public about technology since the 1980s”.
Virtually everything the CCC are involved with stems from a deep desire to draw attention to the misuse of – and security flaws in – the technology that both we and our governments rely on. This is often accompanied with plenty of media coverage, ensuring that any uncovered knowledge reaches as wide an audience as possible.
In the aftermath of the Snowden revelations, the group’s enthusiasm skyrocketed, particularly when the debate turned to mass surveillance, which is where their new focus is centered.
There have to be consequences. The work of intelligence services has to be reviewed – as does their right to exist. If necessary, their aims and methods will have to be redefined. …We have to think about how these [shared] data are processed and where they can be allowed to resurface. And this is not just the challenge for 2015, but for the next 10 years.
CCC Member Falk Garbsch (via DC)
As a few examples of their exploits, in the CCC’s early days, you could expect to see the group protesting against French nuclear tests, s†éáling money live on TV using flaws in Microsoft’s ActiveX technology (1996) andbreaking the COMP128 encryption algorithm of a GSM customer card, unnervingly allowing the card to be cloned (1998).
More recently, in 2008, the CCC highlighted major flaws in a federal trojan horse that the German government was using at the time. This technology was alleged to contravene the ruling of the Constitutional Court with some of it’s flaws being discussed in the group’s press release on the topic:
The malware can not only siphon away intimate data but also offers a remote control or backdoor functionality for uploading and executing arbitrary other programs. Significant design and implementation flaws make all of the functionality available to anyone on the internet.
The CCC’s campaigns weren’t all of this kind, however. One of their early projects involved selling source code obtained illegally from US corporate and government systems, directly to the Soviet KGB, along with a host of other less contentious projects.
As a few instances, “Arcade”was the world’s biggest light show organised by the Chaos Computer Club. The collective also runs a weekly radio show (German), hosts a yearly workshop-based Easter event calledEasterhegg, and puts on Europe’s largest annual häçker gathering, theChaos Communication Congress.
Tarh Andishan: Iran’s Answer To Stuxnet
So far, the attacks mentioned above have rarely, if ever, threatened millions of global citizens with immense danger. In the past couple of years, however, this trend has taken a u-turn with the advent of Tarh Andishan and their relentless pursuit of control over highly important systems and technology.
With an estimated 20 members, most of whom are allegedly based in Tehran, Iran (along with other periphery members around the globe), Tarh Andishan shows what a truly sophisticated häçker group may be capable of.
Angered by a badly damaged computer network thanks to a Stuxnet worm attack (allegedly created by the US and Israel), the Iranian government drastically intensified it’s cyber warfare efforts, and Tahr Andishan— meaning ‘innovators’ in Farsi — was born.
By using automated worm-like propagation systems, backdoors, SQL injection, along with other high-calibre tactics, this group has launched a large number of attacks on prominent agencies, government and military systems, and private companies all over the world under what has been named ‘Operation Cleaver’.
According to the security firm Cylance, Operation Cleaver targeted 16 countries, and suggests that “a new global cyber power has emerged; one that has already compromised some of the world’s most critical infrastructure” including the US Navy’s servers, the systems behind a number of leading global companies, hospitals and universities.
Last year, Cylance’s founder Stuart McClure stated in an interview with the TechTimes that “They aren’t looking for credit cards or microchip designs, they are fortifying their hold on dozens of networks that, if crippled, would affect the lives of billions of people…Over two years ago the Iranians deployed the Shamoon malware on Saudi Aramco, the most destructive attack against a corporate network to date, digitally destroying three-quarters of Aramco’s PCs.”
As a more domestic example of the häçker group’s reach, this collective have also reportedly gained complete access to airline gates and security systems, giving the group ultimate control over passenger/gate credentials. These examples are just a few among many, alluded to in Cylance’s report on Tarh Andishan (PDF). The report claims that he majority of their findings have been left out due to the “grave risk to the physical safety of the world.” that the group now allegedly poses.
The complexity, and horrifying possibilities of Tarh Andishan’s undertakings strongly suggest that this is a state-sponsored häçker collective, with (as of yet) no clear aims or ambitions but with a terrifying ability to compromise even the most secure of systems.
This is Just The Tip Of The Iceberg
These four examples are just the tip of the iceberg when it comes to häçker groups. From Lizard Squad to APT28, the net is awash with groups who’re looking to compromise systems whether for political gain or simply for the lulz. It’s only a relative few, however, who’re responsible for a good chunk of the more publicised attacks that we see in the media. Whether we agree with their approach or not, their capabilities are sometimes shocking, and almost always impressive. The ‘häçker culture’ is not something that’s going away though, and we can only expect to see more of this kind of activity in the future, and it’ll be getting increasingly sophisticated as time goes on.
All we can do is hope that it’s negative results are somehow kept to a minimum.
What do you think of this kind of online activity? Is it an unavoidable aspect of modern technology, or is it something that we have to clamp down on?
Attachments
-
You do not have permission to view the full content of this post. Log in or register now.