J
Jeanh
Guest
PurpleFox anu ba to????? may nag email sa akin...di ko maintindihan
mac2wepkey
Huawei Home Gateway default WEP
Huawei models HG520b, HG520c and HG530
Huawei HG520 and HG530 routers are vulnerable to weak cipher attacks. It is possible to generate the default WEP/WPA key of Huawei HG520 routers. The purpose of this document is to explain the process of developing a key generator for these devices.
Huawei router models HG520b and HG520c contain a key generator command (mac2wepkey) in their TELNET interface. They also contain a command to change the MAC address (fakemac).
It is possible to change our MAC to generate the default WEP key of a MAC of our choosing.
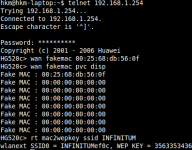
Obtaining the default WEP and SSID of another MAC address
This was published by adiaz last August in You do not have permission to view the full content of this post. Log in or register now.. Over the past few months we have been working on obtaining the algorithm to create our own key generator and we finally made it!
The first step was generating some lists containing MAC, SSID and WEP keys of about 200 entries and trying to identify patterns. The first thing we noticed was that the WEP key had values from 30 to 39 and from 61 to 66. These values correspond to the numbers 1 to 9 and letters a-f in ASCII.

Default WEP KEY and SSID in Huawei routers
After analyzing the lists we noticed that the numbers are repeated in pairs, so by forming several lists we could predict the next SSID and WEP key. Then by looking at how the bits changed, we were able to identify the XOR function.
The first lists were generated with the help of the mac2wepkey command in the TELNET interface of the modem. The lists were generated for the first byte of the MAC address:
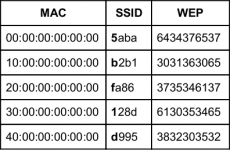
With MAC 00:00:00:00:00:00 we get the base SSID (5aba) and base WEP (6434376537).
To reduce the amount of generated lists, we will use the XOR operation. The XOR operation is a reversible function defined as a^b=d and b^d=a. Since there are patterns on the lists, this will create repeated lists simplifying the amount of unique lists required. We will need to apply the XOR function to obtain the final value.
9 bytes are generated for each position of the MAC address (4 bytes for the SSID and 5 bytes for the WEP key). This totals 108 lists (9x12). You can see the 108 lists that already have the XOR base applied in
You do not have permission to view the full content of this post. Log in or register now.
This is the list for the first position of the MAC address (Ex. 52:00:00:00:00:00) the value is 5 so we will use the values in position 6 of the list:
SSID-A [0, 14, 10, 4, 8, 6, 2, 12, 0, 14, 10, 4, 8, 6, 2, 12]
SSID-B [0, 8, 0, 8, 3, 11, 3, 11, 6, 14, 6, 14, 5, 13, 5, 13]
SSID-C [0, 0, 3, 3, 2, 2, 1, 1, 4, 4, 7, 7, 6, 6, 5, 5]
SSID-D [0, 11, 12, 7, 15, 4, 3, 8, 14, 5, 2, 9, 1, 10, 13, 6]
WEP-A [0, 13, 10, 7, 5, 8, 15, 2, 10, 7, 0, 13, 15, 2, 5, 8]
WEP-B [0, 5, 1, 4, 6, 3, 7, 2, 12, 9, 13, 8, 10, 15, 11, 14]
WEP-C [0, 1, 3, 2, 7, 6, 4, 5, 15, 14, 12, 13, 8, 9, 11, 10]
WEP-D [0, 14, 4, 10, 11, 5, 15, 1, 6, 8, 2, 12, 13, 3, 9, 7]
WEP-E [0, 9, 0, 9, 5, 12, 5, 12, 10, 3, 10, 3, 15, 6, 15, 6]
The following list is for the second position of the MAC address (Ex. 52:00:00:00:00:00) the value is 2 so we will use the values of position 3 in the list:
SSID-A [0, 5, 11, 14, 7, 2, 12, 9, 15, 10, 4, 1, 8, 13, 3, 6]
SSID-B [0, 5, 11, 14, 2, 7, 9, 12, 12, 9, 7, 2, 14, 11, 5, 0]
SSID-C [0, 0, 0, 0, 4, 4, 4, 4, 0, 0, 0, 0, 4, 4, 4, 4]
SSID-D [0, 8, 1, 9, 3, 11, 2, 10, 5, 13, 4, 12, 6, 14, 7, 15]
WEP-A [0, 14, 13, 3, 9, 7, 4, 10, 6, 8, 11, 5, 15, 1, 2, 12]
WEP-B [0, 13, 10, 7, 4, 9, 14, 3, 10, 7, 0, 13, 14, 3, 4, 9]
WEP-C [0, 4, 8, 12, 0, 4, 8, 12, 0, 4, 8, 12, 0, 4, 8, 12]
WEP-D [0, 1, 3, 2, 6, 7, 5, 4, 15, 14, 12, 13, 9, 8, 10, 11]
WEP-E[0, 1, 3, 2, 4, 5, 7, 6, 12, 13, 15, 14, 8, 9, 11, 10]
All other positions have the value 0. This value corresponds to 0 in every other list, so the final equation for the first byte of the SSID is the following:
6^11^0^0^0^0^0^0^0^0^0^0^(5 base)= 8 [SSID=8A9F]
From the 108 lists we generated, there are 16 lists that are repeated that we will note with the letter A (A1, A2, A3...) and 33 lists that are never repeated that we will note with the letter N (N1, N2...). This totals 49 unique lists.
Now for a complete example we will use MAC(x): 81:23:45:AB:CD:EF
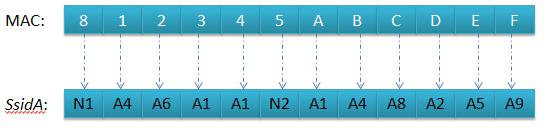
Each byte corresponds to a different list
The list SsidA contains the necessary lists to obtain the first character of the SSID. The first byte of the MAC corresponds to the list N1.
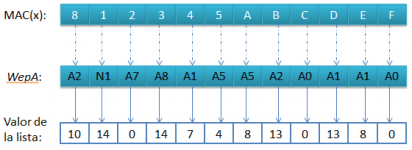
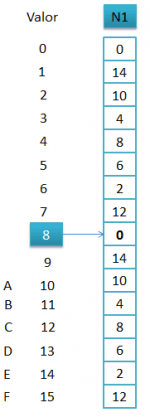
The value of the first byte is 8, if we look it up on the list N1, its value corresponds to 0.
In the same way we obtain each value for all 12 bytes of the MAC address.
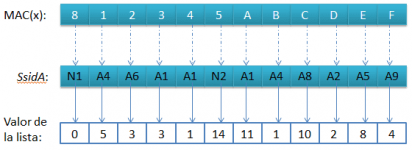
Once we have all 12 values, we apply XOR adding the first byte of the base SSID (5aba).
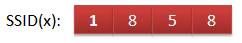
This results in a value of 1, which is the first byte of the final SSID(x). We repeat the same process for all 4 SSID lists and we obtain:
In order to obtain the values of the WEP key, we use the same process. First we obtain, for the first byte of the WEP key, all corresponding values from their lists.
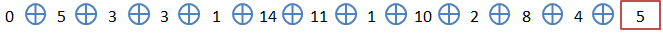
Once we have all 12 values we apply XOR adding the first byte of the base WEP (6434376537). This first byte is 64 in ASCII so it is d en HEXADECIMAL and 13 in DECIMAL.

As a result we get 4. Converted back to ASCII is 34 which corresponds to the first byte of the WEP key.
We repeat this process for all 5 lists for the WEP key and we obtain the final default WEP:

We have developed the key generator in several languages; we will share the python version now: You do not have permission to view the full content of this post. Log in or register now.

# mac2wepkey Huawei HG520 by hochoa@websec.mx - 12/2010
i=0;mac=[]
a0=0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0
a1=0,1,2,3,4,5,6,7,8,9,10,11,12,13,14,15
a2=0,13,10,7,5,8,15,2,10,7,0,13,15,2,5,8
a3=0,1,3,2,7,6,4,5,15,14,12,13,8,9,11,10
a4=0,5,11,14,7,2,12,9,15,10,4,1,8,13,3,6
a5=0,4,8,12,0,4,8,12,0,4,8,12,0,4,8,12
a6=0,1,3,2,6,7,5,4,12,13,15,14,10,11,9,8
a7=0,8,0,8,1,9,1,9,2,10,2,10,3,11,3,11
a8=0,5,11,14,6,3,13,8,12,9,7,2,10,15,1,4
a9=0,9,2,11,5,12,7,14,10,3,8,1,15,6,13,4
a10=0,14,13,3,11,5,6,8,6,8,11,5,13,3,0,14
a11=0,12,8,4,1,13,9,5,2,14,10,6,3,15,11,7
a12=0,4,9,13,2,6,11,15,4,0,13,9,6,2,15,11
a13=0,8,1,9,3,11,2,10,6,14,7,15,5,13,4,12
a14=0,1,3,2,7,6,4,5,14,15,13,12,9,8,10,11
a15=0,1,3,2,6,7,5,4,13,12,14,15,11,10,8,9
n1=0,14,10,4,8,6,2,12,0,14,10,4,8,6,2,12
n2=0,8,0,8,3,11,3,11,6,14,6,14,5,13,5,13
n3=0,0,3,3,2,2,1,1,4,4,7,7,6,6,5,5
n4=0,11,12,7,15,4,3,8,14,5,2,9,1,10,13,6
n5=0,5,1,4,6,3,7,2,12,9,13,8,10,15,11,14
n6=0,14,4,10,11,5,15,1,6,8,2,12,13,3,9,7
n7=0,9,0,9,5,12,5,12,10,3,10,3,15,6,15,6
n8=0,5,11,14,2,7,9,12,12,9,7,2,14,11,5,0
n9=0,0,0,0,4,4,4,4,0,0,0,0,4,4,4,4
n10=0,8,1,9,3,11,2,10,5,13,4,12,6,14,7,15
n11=0,14,13,3,9,7,4,10,6,8,11,5,15,1,2,12
n12=0,13,10,7,4,9,14,3,10,7,0,13,14,3,4,9
n13=0,1,3,2,6,7,5,4,15,14,12,13,9,8,10,11
n14=0,1,3,2,4,5,7,6,12,13,15,14,8,9,11,10
n15=0,6,12,10,9,15,5,3,2,4,14,8,11,13,7,1
n16=0,11,6,13,13,6,11,0,11,0,13,6,6,13,0,11
n17=0,12,8,4,1,13,9,5,3,15,11,7,2,14,10,6
n18=0,12,9,5,2,14,11,7,5,9,12,0,7,11,14,2
n19=0,6,13,11,10,12,7,1,5,3,8,14,15,9,2,4
n20=0,9,3,10,7,14,4,13,14,7,13,4,9,0,10,3
n21=0,4,8,12,1,5,9,13,2,6,10,14,3,7,11,15
n22=0,1,2,3,5,4,7,6,11,10,9,8,14,15,12,13
n23=0,7,15,8,14,9,1,6,12,11,3,4,2,5,13,10
n24=0,5,10,15,4,1,14,11,8,13,2,7,12,9,6,3
n25=0,11,6,13,13,6,11,0,10,1,12,7,7,12,1,10
n26=0,13,10,7,4,9,14,3,8,5,2,15,12,1,6,11
n27=0,4,9,13,2,6,11,15,5,1,12,8,7,3,14,10
n28=0,14,12,2,8,6,4,10,0,14,12,2,8,6,4,10
n29=0,0,0,0,1,1,1,1,2,2,2,2,3,3,3,3
n30=0,15,14,1,12,3,2,13,8,7,6,9,4,11,10,5
n31=0,10,4,14,9,3,13,7,2,8,6,12,11,1,15,5
n32=0,10,5,15,11,1,14,4,6,12,3,9,13,7,8,2
n33=0,4,9,13,3,7,10,14,7,3,14,10,4,0,13,9
key=30,31,32,33,34,35,36,37,38,39,61,62,63,64,65,66
ssid=[0,1,2,3,4,5,6,7,8,9,'a','b','c','d','e','f']
def hex2dec(s):
return int(s, 16)
print "\n
- See more at: You do not have permission to view the full content of this post. Log in or register now.
@miyasaki
mac2wepkey
Huawei Home Gateway default WEP
Huawei models HG520b, HG520c and HG530
Huawei HG520 and HG530 routers are vulnerable to weak cipher attacks. It is possible to generate the default WEP/WPA key of Huawei HG520 routers. The purpose of this document is to explain the process of developing a key generator for these devices.
Huawei router models HG520b and HG520c contain a key generator command (mac2wepkey) in their TELNET interface. They also contain a command to change the MAC address (fakemac).
It is possible to change our MAC to generate the default WEP key of a MAC of our choosing.

Obtaining the default WEP and SSID of another MAC address
This was published by adiaz last August in You do not have permission to view the full content of this post. Log in or register now.. Over the past few months we have been working on obtaining the algorithm to create our own key generator and we finally made it!
The first step was generating some lists containing MAC, SSID and WEP keys of about 200 entries and trying to identify patterns. The first thing we noticed was that the WEP key had values from 30 to 39 and from 61 to 66. These values correspond to the numbers 1 to 9 and letters a-f in ASCII.

Default WEP KEY and SSID in Huawei routers
After analyzing the lists we noticed that the numbers are repeated in pairs, so by forming several lists we could predict the next SSID and WEP key. Then by looking at how the bits changed, we were able to identify the XOR function.
The first lists were generated with the help of the mac2wepkey command in the TELNET interface of the modem. The lists were generated for the first byte of the MAC address:

With MAC 00:00:00:00:00:00 we get the base SSID (5aba) and base WEP (6434376537).
To reduce the amount of generated lists, we will use the XOR operation. The XOR operation is a reversible function defined as a^b=d and b^d=a. Since there are patterns on the lists, this will create repeated lists simplifying the amount of unique lists required. We will need to apply the XOR function to obtain the final value.
9 bytes are generated for each position of the MAC address (4 bytes for the SSID and 5 bytes for the WEP key). This totals 108 lists (9x12). You can see the 108 lists that already have the XOR base applied in
You do not have permission to view the full content of this post. Log in or register now.
This is the list for the first position of the MAC address (Ex. 52:00:00:00:00:00) the value is 5 so we will use the values in position 6 of the list:
SSID-A [0, 14, 10, 4, 8, 6, 2, 12, 0, 14, 10, 4, 8, 6, 2, 12]
SSID-B [0, 8, 0, 8, 3, 11, 3, 11, 6, 14, 6, 14, 5, 13, 5, 13]
SSID-C [0, 0, 3, 3, 2, 2, 1, 1, 4, 4, 7, 7, 6, 6, 5, 5]
SSID-D [0, 11, 12, 7, 15, 4, 3, 8, 14, 5, 2, 9, 1, 10, 13, 6]
WEP-A [0, 13, 10, 7, 5, 8, 15, 2, 10, 7, 0, 13, 15, 2, 5, 8]
WEP-B [0, 5, 1, 4, 6, 3, 7, 2, 12, 9, 13, 8, 10, 15, 11, 14]
WEP-C [0, 1, 3, 2, 7, 6, 4, 5, 15, 14, 12, 13, 8, 9, 11, 10]
WEP-D [0, 14, 4, 10, 11, 5, 15, 1, 6, 8, 2, 12, 13, 3, 9, 7]
WEP-E [0, 9, 0, 9, 5, 12, 5, 12, 10, 3, 10, 3, 15, 6, 15, 6]
The following list is for the second position of the MAC address (Ex. 52:00:00:00:00:00) the value is 2 so we will use the values of position 3 in the list:
SSID-A [0, 5, 11, 14, 7, 2, 12, 9, 15, 10, 4, 1, 8, 13, 3, 6]
SSID-B [0, 5, 11, 14, 2, 7, 9, 12, 12, 9, 7, 2, 14, 11, 5, 0]
SSID-C [0, 0, 0, 0, 4, 4, 4, 4, 0, 0, 0, 0, 4, 4, 4, 4]
SSID-D [0, 8, 1, 9, 3, 11, 2, 10, 5, 13, 4, 12, 6, 14, 7, 15]
WEP-A [0, 14, 13, 3, 9, 7, 4, 10, 6, 8, 11, 5, 15, 1, 2, 12]
WEP-B [0, 13, 10, 7, 4, 9, 14, 3, 10, 7, 0, 13, 14, 3, 4, 9]
WEP-C [0, 4, 8, 12, 0, 4, 8, 12, 0, 4, 8, 12, 0, 4, 8, 12]
WEP-D [0, 1, 3, 2, 6, 7, 5, 4, 15, 14, 12, 13, 9, 8, 10, 11]
WEP-E[0, 1, 3, 2, 4, 5, 7, 6, 12, 13, 15, 14, 8, 9, 11, 10]
All other positions have the value 0. This value corresponds to 0 in every other list, so the final equation for the first byte of the SSID is the following:
6^11^0^0^0^0^0^0^0^0^0^0^(5 base)= 8 [SSID=8A9F]
From the 108 lists we generated, there are 16 lists that are repeated that we will note with the letter A (A1, A2, A3...) and 33 lists that are never repeated that we will note with the letter N (N1, N2...). This totals 49 unique lists.
Now for a complete example we will use MAC(x): 81:23:45:AB:CD:EF

Each byte corresponds to a different list
The list SsidA contains the necessary lists to obtain the first character of the SSID. The first byte of the MAC corresponds to the list N1.

The value of the first byte is 8, if we look it up on the list N1, its value corresponds to 0.
In the same way we obtain each value for all 12 bytes of the MAC address.

Once we have all 12 values, we apply XOR adding the first byte of the base SSID (5aba).

This results in a value of 1, which is the first byte of the final SSID(x). We repeat the same process for all 4 SSID lists and we obtain:
In order to obtain the values of the WEP key, we use the same process. First we obtain, for the first byte of the WEP key, all corresponding values from their lists.
Once we have all 12 values we apply XOR adding the first byte of the base WEP (6434376537). This first byte is 64 in ASCII so it is d en HEXADECIMAL and 13 in DECIMAL.

As a result we get 4. Converted back to ASCII is 34 which corresponds to the first byte of the WEP key.
We repeat this process for all 5 lists for the WEP key and we obtain the final default WEP:
We have developed the key generator in several languages; we will share the python version now: You do not have permission to view the full content of this post. Log in or register now.
# mac2wepkey Huawei HG520 by hochoa@websec.mx - 12/2010
i=0;mac=[]
a0=0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0
a1=0,1,2,3,4,5,6,7,8,9,10,11,12,13,14,15
a2=0,13,10,7,5,8,15,2,10,7,0,13,15,2,5,8
a3=0,1,3,2,7,6,4,5,15,14,12,13,8,9,11,10
a4=0,5,11,14,7,2,12,9,15,10,4,1,8,13,3,6
a5=0,4,8,12,0,4,8,12,0,4,8,12,0,4,8,12
a6=0,1,3,2,6,7,5,4,12,13,15,14,10,11,9,8
a7=0,8,0,8,1,9,1,9,2,10,2,10,3,11,3,11
a8=0,5,11,14,6,3,13,8,12,9,7,2,10,15,1,4
a9=0,9,2,11,5,12,7,14,10,3,8,1,15,6,13,4
a10=0,14,13,3,11,5,6,8,6,8,11,5,13,3,0,14
a11=0,12,8,4,1,13,9,5,2,14,10,6,3,15,11,7
a12=0,4,9,13,2,6,11,15,4,0,13,9,6,2,15,11
a13=0,8,1,9,3,11,2,10,6,14,7,15,5,13,4,12
a14=0,1,3,2,7,6,4,5,14,15,13,12,9,8,10,11
a15=0,1,3,2,6,7,5,4,13,12,14,15,11,10,8,9
n1=0,14,10,4,8,6,2,12,0,14,10,4,8,6,2,12
n2=0,8,0,8,3,11,3,11,6,14,6,14,5,13,5,13
n3=0,0,3,3,2,2,1,1,4,4,7,7,6,6,5,5
n4=0,11,12,7,15,4,3,8,14,5,2,9,1,10,13,6
n5=0,5,1,4,6,3,7,2,12,9,13,8,10,15,11,14
n6=0,14,4,10,11,5,15,1,6,8,2,12,13,3,9,7
n7=0,9,0,9,5,12,5,12,10,3,10,3,15,6,15,6
n8=0,5,11,14,2,7,9,12,12,9,7,2,14,11,5,0
n9=0,0,0,0,4,4,4,4,0,0,0,0,4,4,4,4
n10=0,8,1,9,3,11,2,10,5,13,4,12,6,14,7,15
n11=0,14,13,3,9,7,4,10,6,8,11,5,15,1,2,12
n12=0,13,10,7,4,9,14,3,10,7,0,13,14,3,4,9
n13=0,1,3,2,6,7,5,4,15,14,12,13,9,8,10,11
n14=0,1,3,2,4,5,7,6,12,13,15,14,8,9,11,10
n15=0,6,12,10,9,15,5,3,2,4,14,8,11,13,7,1
n16=0,11,6,13,13,6,11,0,11,0,13,6,6,13,0,11
n17=0,12,8,4,1,13,9,5,3,15,11,7,2,14,10,6
n18=0,12,9,5,2,14,11,7,5,9,12,0,7,11,14,2
n19=0,6,13,11,10,12,7,1,5,3,8,14,15,9,2,4
n20=0,9,3,10,7,14,4,13,14,7,13,4,9,0,10,3
n21=0,4,8,12,1,5,9,13,2,6,10,14,3,7,11,15
n22=0,1,2,3,5,4,7,6,11,10,9,8,14,15,12,13
n23=0,7,15,8,14,9,1,6,12,11,3,4,2,5,13,10
n24=0,5,10,15,4,1,14,11,8,13,2,7,12,9,6,3
n25=0,11,6,13,13,6,11,0,10,1,12,7,7,12,1,10
n26=0,13,10,7,4,9,14,3,8,5,2,15,12,1,6,11
n27=0,4,9,13,2,6,11,15,5,1,12,8,7,3,14,10
n28=0,14,12,2,8,6,4,10,0,14,12,2,8,6,4,10
n29=0,0,0,0,1,1,1,1,2,2,2,2,3,3,3,3
n30=0,15,14,1,12,3,2,13,8,7,6,9,4,11,10,5
n31=0,10,4,14,9,3,13,7,2,8,6,12,11,1,15,5
n32=0,10,5,15,11,1,14,4,6,12,3,9,13,7,8,2
n33=0,4,9,13,3,7,10,14,7,3,14,10,4,0,13,9
key=30,31,32,33,34,35,36,37,38,39,61,62,63,64,65,66
ssid=[0,1,2,3,4,5,6,7,8,9,'a','b','c','d','e','f']
def hex2dec(s):
return int(s, 16)
print "\n
- See more at: You do not have permission to view the full content of this post. Log in or register now.
@miyasaki
Attachments
-
You do not have permission to view the full content of this post. Log in or register now.