Eto na...
Review
Requirements
-RawCap.exe
-(optional) notepad ++
-HPI
-Target config
-Administrator access
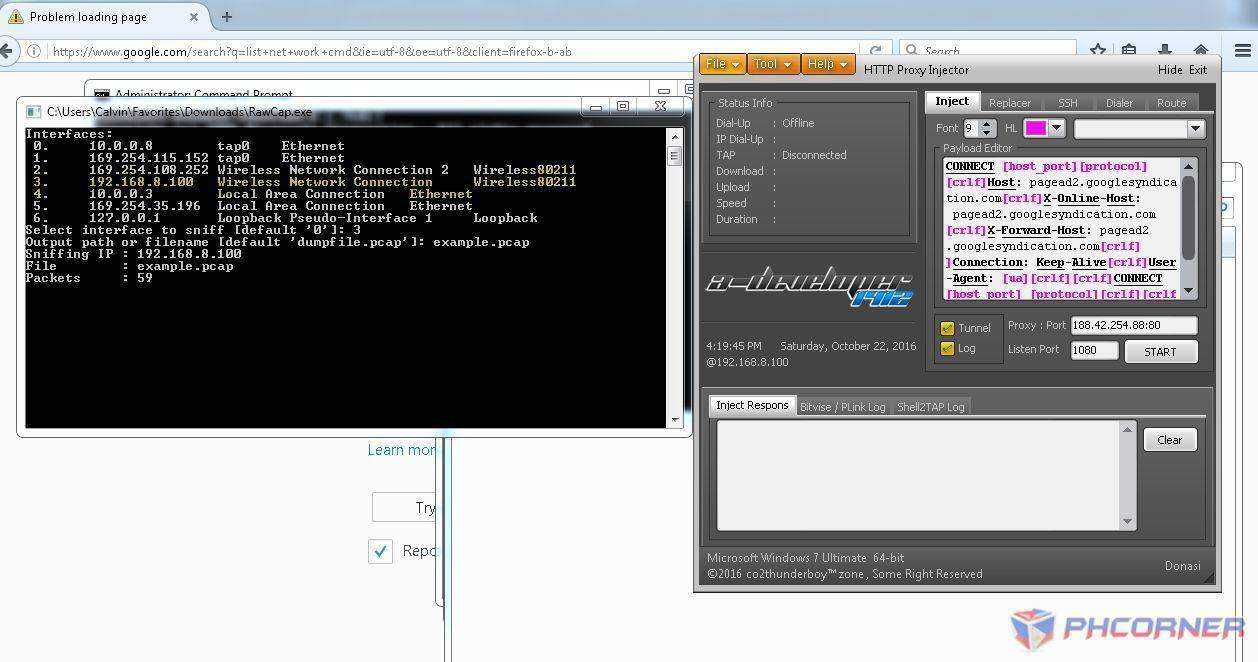
First open RawCap and HPI
in raw cap kaylangan natin pumili ng interface. Yan yung adapter kung san ka nakaconect.
Para mas madale hanapin mo yung IPv4 ng modem or wifi mo. In my case 192.168.8.100.
Ok kung di mo pa din alam, go to control panel>network and sharing under "view your active networks">"connections" double click mo yung Wireless network kung naka wifi ka.
then, click details, here you can see the IPv4 take note of that.
Let's go back
type and enter the number that corresponds to your connection in my case 3
Then type and enter [whatever].pcap. For the sake of this tutorial I used example.pcap
Go to your HPI make sure na check ang tunnel at log.
Go to Bitvise / Plink log tab para makita mo ang IP ng ssh ng target mo. Magagamit mo to para madaling hanapin mamaya ang payload.
then Click start.. take note of the IP, better copy it...
Next Hintayin mo lang na kumonek o mag error...
Kung kumonek (mangyayare yun kung di pa expired), surf surf ka muna. Check mo kung ilan na nacacapture na packets sa RawCap i recommend more than a thousand before stopping.
Kung di kumonek, stop-start nyo lang hanggang sa dumami ng dumami ang packets sa RawCap.
Kung Ok na. Go back to RawCap and press CTRL+C.
Head over to the location of your RawCap (e.g. Desktop) and find the [whatever].pcap file and open it using a text editor (I'll be using notepad ++)
Hit CTRL+F and paste mo yung IP na kinopy natin kanina then hit enter.
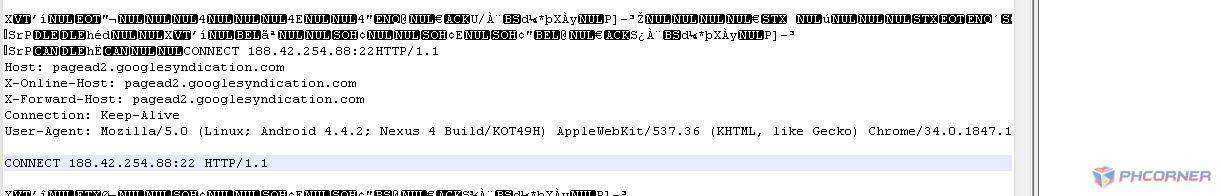
Hanap ka ng medyo malinaw. Eto resulta ng aking example
Next step ay itranslate ito..
Kung my alam ka na sa payload pwede ka na mag skip kasi alam mo na ang mga susunod.
Sa example makikita na ang request method ay CONNECT at normal ang injection. makikita rin na may roong X-Online-Host, X-Forward-Host, User-Agent, at Keep-Alive na nag mamatch doon sa first picture.
Ibig sabihin kung gagamit ng generator request:connect injection:normal at ichecheck ang X-Online-Host, X-Forward-Host, User-Agent, at Keep-Alive. At syempre ika copy paste natin yung host (sa example pagead2.googlesyndication.com).
Tip: 1enter=1[crlf]
Connect xxx.xxx.xxx.xxx:xxx HTTP/1.1=CONNECT [host_port][protocol]
Example:
CONNECT xxx.xxx.xxx.xxx:xxx HTTP/1.1
Host: pogiako.com
X-Online-Host: pogiako.com
CONNECT xxx.xxx.xxx.xxx:xxx HTTP/1.1
equivalent to...
CONNECT [host_port][protocol][crlf]Host: pogiako.com[crlf]X-Online-Host: pogiako.com[crlf][crlf]CONNECT [host_port][protocol]
Thanks
Sa magaling sa payload paturo uuyyy.. gusto ko yung manomano
Review
Requirements
-RawCap.exe
-(optional) notepad ++
-HPI
-Target config
-Administrator access
First open RawCap and HPI
in raw cap kaylangan natin pumili ng interface. Yan yung adapter kung san ka nakaconect.
Para mas madale hanapin mo yung IPv4 ng modem or wifi mo. In my case 192.168.8.100.
Ok kung di mo pa din alam, go to control panel>network and sharing under "view your active networks">"connections" double click mo yung Wireless network kung naka wifi ka.
then, click details, here you can see the IPv4 take note of that.
Let's go back
type and enter the number that corresponds to your connection in my case 3
Then type and enter [whatever].pcap. For the sake of this tutorial I used example.pcap
Go to your HPI make sure na check ang tunnel at log.
Go to Bitvise / Plink log tab para makita mo ang IP ng ssh ng target mo. Magagamit mo to para madaling hanapin mamaya ang payload.
then Click start.. take note of the IP, better copy it...
Next Hintayin mo lang na kumonek o mag error...
Kung kumonek (mangyayare yun kung di pa expired), surf surf ka muna. Check mo kung ilan na nacacapture na packets sa RawCap i recommend more than a thousand before stopping.
Kung di kumonek, stop-start nyo lang hanggang sa dumami ng dumami ang packets sa RawCap.
Kung Ok na. Go back to RawCap and press CTRL+C.
Head over to the location of your RawCap (e.g. Desktop) and find the [whatever].pcap file and open it using a text editor (I'll be using notepad ++)
Hit CTRL+F and paste mo yung IP na kinopy natin kanina then hit enter.
Hanap ka ng medyo malinaw. Eto resulta ng aking example
Next step ay itranslate ito..
Kung my alam ka na sa payload pwede ka na mag skip kasi alam mo na ang mga susunod.
Sa example makikita na ang request method ay CONNECT at normal ang injection. makikita rin na may roong X-Online-Host, X-Forward-Host, User-Agent, at Keep-Alive na nag mamatch doon sa first picture.
Ibig sabihin kung gagamit ng generator request:connect injection:normal at ichecheck ang X-Online-Host, X-Forward-Host, User-Agent, at Keep-Alive. At syempre ika copy paste natin yung host (sa example pagead2.googlesyndication.com).
Tip: 1enter=1[crlf]
Connect xxx.xxx.xxx.xxx:xxx HTTP/1.1=CONNECT [host_port][protocol]
Example:
CONNECT xxx.xxx.xxx.xxx:xxx HTTP/1.1
Host: pogiako.com
X-Online-Host: pogiako.com
CONNECT xxx.xxx.xxx.xxx:xxx HTTP/1.1
equivalent to...
CONNECT [host_port][protocol][crlf]Host: pogiako.com[crlf]X-Online-Host: pogiako.com[crlf][crlf]CONNECT [host_port][protocol]
Thanks
Sa magaling sa payload paturo uuyyy.. gusto ko yung manomano
Attachments
-
You do not have permission to view the full content of this post. Log in or register now.
Last edited: